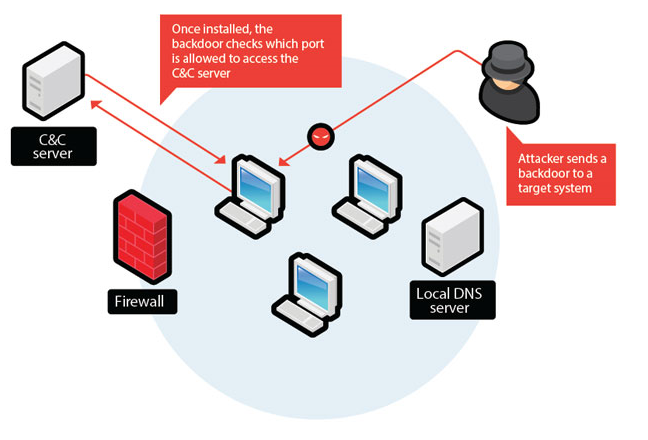
A backdoor, also known as a trapdoor, is a way to access a computer software without getting detected or stopped by security programs installed on the PC. This term can refer to both the legitimate means of access as well as the applications that are used for remote attacks by hackers. Legitimate undocumented backdoors are used in order to allow the administrator to enter a computer system for troubleshooting, upkeep, or other reasons. Secret portals that are used by cyber criminals, on the other hand, can allow them to enter computers for malicious purposes.
Built-in legitimate backdoors are generally used for maintenance. Some of them are protected by a username and a password. In most cases, users have no idea that these backdoors exist, and only the makers of the programs are aware of them. Backdoors were a hot topic back in 2013, when Edward Snowden released the information about the NSA’s effort to make companies install backdoors into their software. These backdoors would allow the intelligence agencies to enter systems unnoticed and access the data necessary to them.
The 10 biggest software backdoors of all time
- Back Orifice
- The DSL backdoor that wouldn’t die
- The PGP full-disk encryption backdoor
- Backdoors in pirated copies of commercial WordPress plug-ins
- The Joomla plug-in backdoor
- The ProFTPD backdoor
- The Borland Interbase backdoor
- The Linux backdoor ( insert a subtle backdoor)
- The tcpdump backdoor
- The Flawed hardening backdoor
Although administrative backdoors also create vulnerabilities in software and systems, the real trouble comes when hackers install their own backdoors onto the computer. Cyber criminals can use backdoors in order to access the system without the user’s notice and steal their personal data as well as drop other malicious applications onto the PC. Both of these actions can lead to serious consequences. If cyber crooks gain access to the user’s personal information, this can result in identity theft or financial losses, while the addition of other malware onto the computer could result in system damage, data corruption, browsing issues, and more.
What should be a priority for computer users is that they install reliable anti-malware tools capable of detecting backdoors and eliminating them from the system and keep these tools updated. This would ensure that they do not have to deal with the above-mentioned problems. If you think that there may be malicious programs on your PC already, you should download and implement the malware prevention and removal tool as soon as you can. It will help you detect backdoors and other threats, clean your computer, and keep it safeguarded from future attacks.
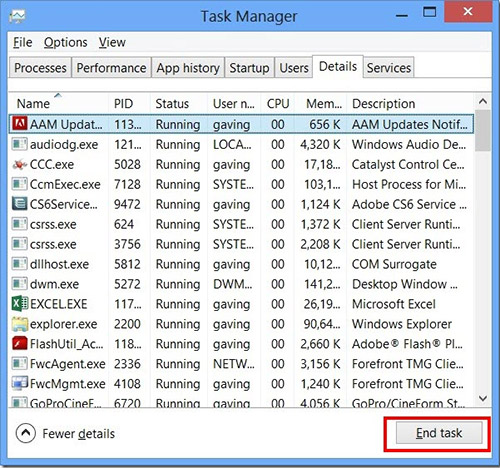
Step 1: Stop all What is Backdoors? The 10 biggest backdoors processes in Task Manager
- Press and hold Ctrl+Alt+Del to open Task Manager
- Go to Details tab and end all What is Backdoors? The 10 biggest backdoors related processes (select the process and click End Task)
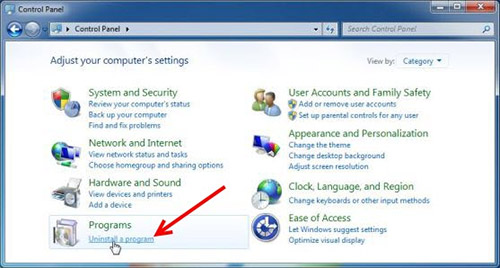
Step 2: Remove What is Backdoors? The 10 biggest backdoors related programs
- Click Start and open Control Panel
- Select Uninstall a program under Programs
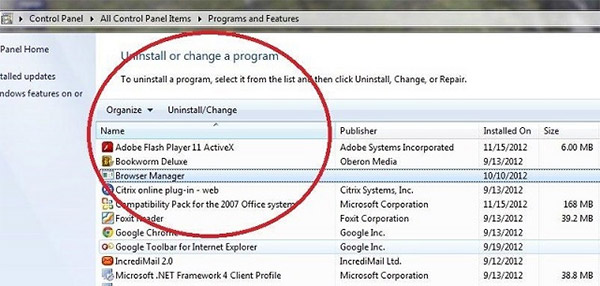
- Choose the suspicious software and click Uninstall/Change
Step 3: Delete malicious What is Backdoors? The 10 biggest backdoors entries in the system Registry
- Tap Win+R to open Run, type in ‘regedit’ and click OK
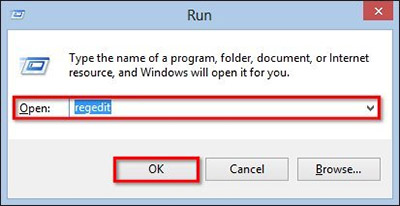
- If User Account Control pops up, click OK
- Once in the Registry Editor, delete all What is Backdoors? The 10 biggest backdoors related entries
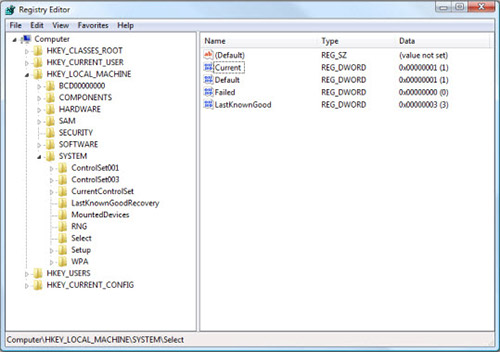
Step 4: Eliminate malicious files and folders related to What is Backdoors? The 10 biggest backdoors
- Click Start and open Control Panel
- Click on View by, select Large icons and open Folder Options
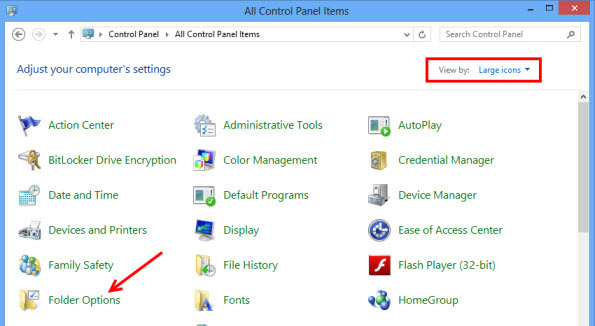
- Go to the View tab, check Show hidden files, folders or drivers and click OK
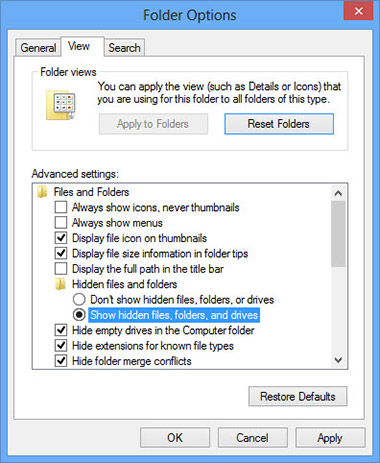
- Delete all What is Backdoors? The 10 biggest backdoors related folders and files
%AllUsersProfile%\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
Step5: Remove What is Backdoors? The 10 biggest backdoors from your browsers
Download Removal Toolto remove this ThreatInternet Explorer
- Launch Internet Explorer, click on the Gear icon → Manage add-ons
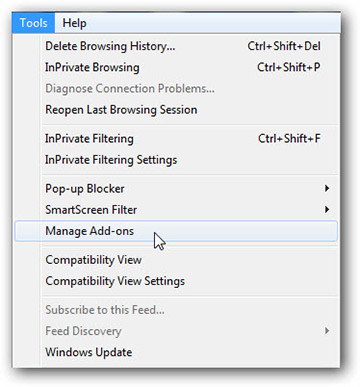
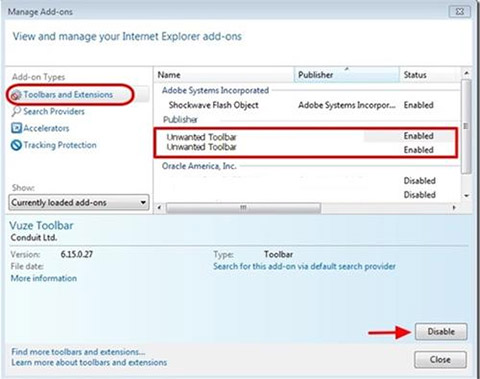
- Choose Toolbars and Extensions section and disable suspicious extensions
Mozilla Firefox
- Open Mozilla, tap Ctrl+Shift+A and go to Extensions
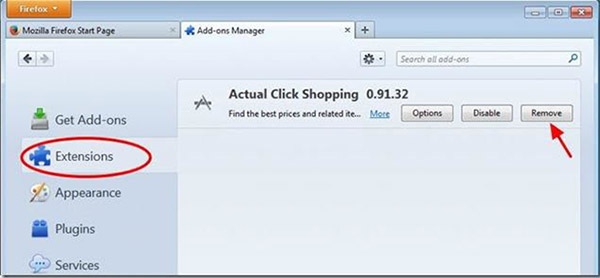
- Select and remove all unwanted extensions
Google Chrome
- Open your browser, click on the menu and select Tools → Extensions
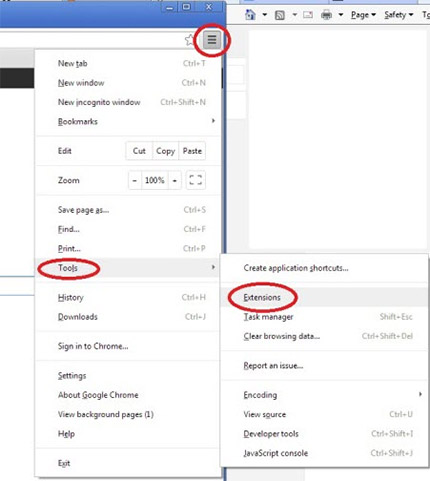
- Choose the suspicious add-on and click on the Trash can icon to remove it
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.